TonUP质押池攻击事件简要分析
- B1ue1nWh1te
- 更新于 2024-05-27 10:46
- 阅读 939
今天刷资讯看到TonUP项目被黑了,最近正好在了解TON生态,于是考虑简单分析一波。相关资讯1相关资讯2被攻击的一个主要质押池合约:EQAxN5aREN_WF-He1uKeQsalDxobF3kz2u-5U69x_RAzK3sQ攻击者:UQCqfGGPYqDhFC2-6FcAld
前几天刷资讯看到TonUP项目被黑了,最近正好在了解TON生态,于是考虑简单分析一波。
被攻击的一个主要质押池合约:EQAxN5aREN_WF-He1uKeQsalDxobF3kz2u-5U69x_RAzK3sQ
攻击者:UQCqfGGPYqDhFC2-6FcAldnWwkKHcs_Ez9RoXvJF_in3y_ll
白帽救援者:notcoin-scam.ton
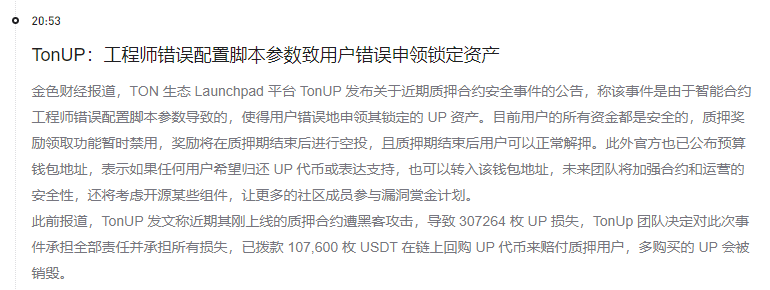
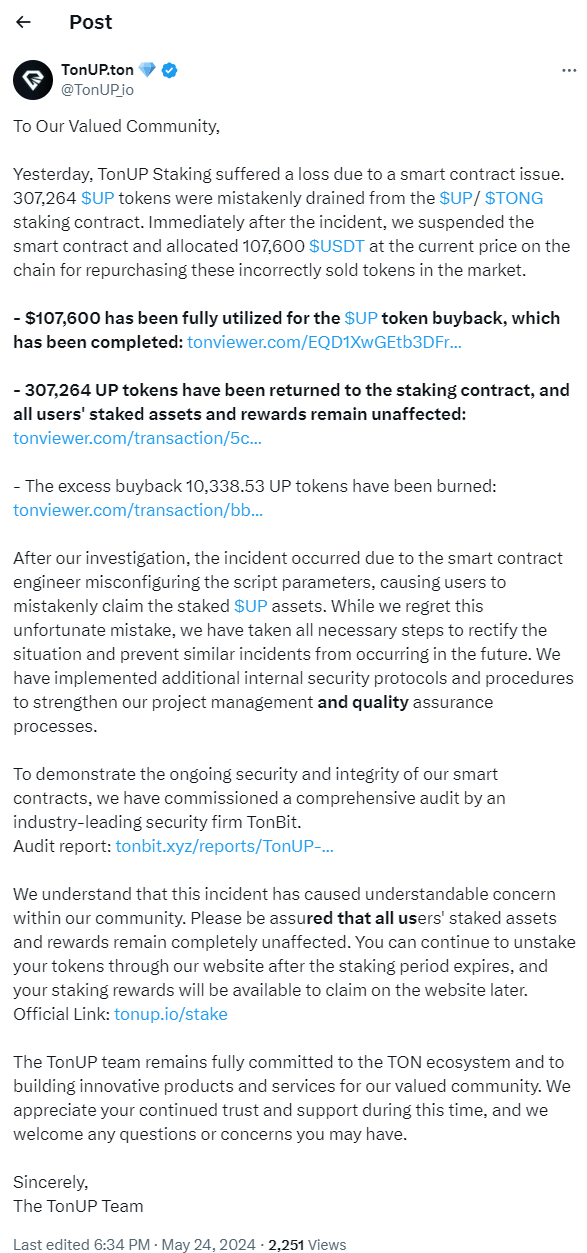
1.攻击者向[TonUP 功能合约-EQDPNq_v_rCljQzrueWeIxACBVgWlJr0qtXwaZSipMRIj7pQ]发送"I accept the ToS of TonUP. SHA256:8a5b220..37b75ca."消息进行注册,这是一个惯例操作,用于表示同意服务条款以便使用网站服务。
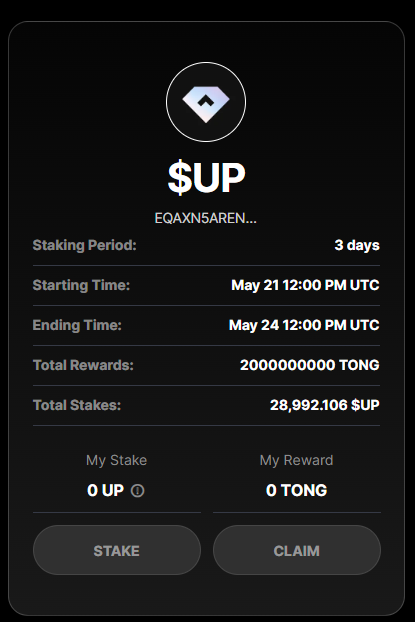
2.攻击者尝试以发送消息的形式调用[UP 质押池合约-EQAxN5aREN_WF-He1uKeQsalDxobF3kz2u-5U69x_RAzK3sQ]的claim函数,结果意外地接收到了当时质押池中已由其他用户存入的所有[UP 代币-EQCvaf0JMrv6BOvPpAgee08uQMuRpUd__fhA7Nm8twzvbE]。
由于质押池相关的合约均未开源,基于结果来猜测应该是某些参数配置错误导致了用户在claim的时候会获得质押池合约中的所有UP代币。这似乎是一个不需要什么技术分析的简单漏洞,任何人都可以通过发送同样的消息来简单地利用。
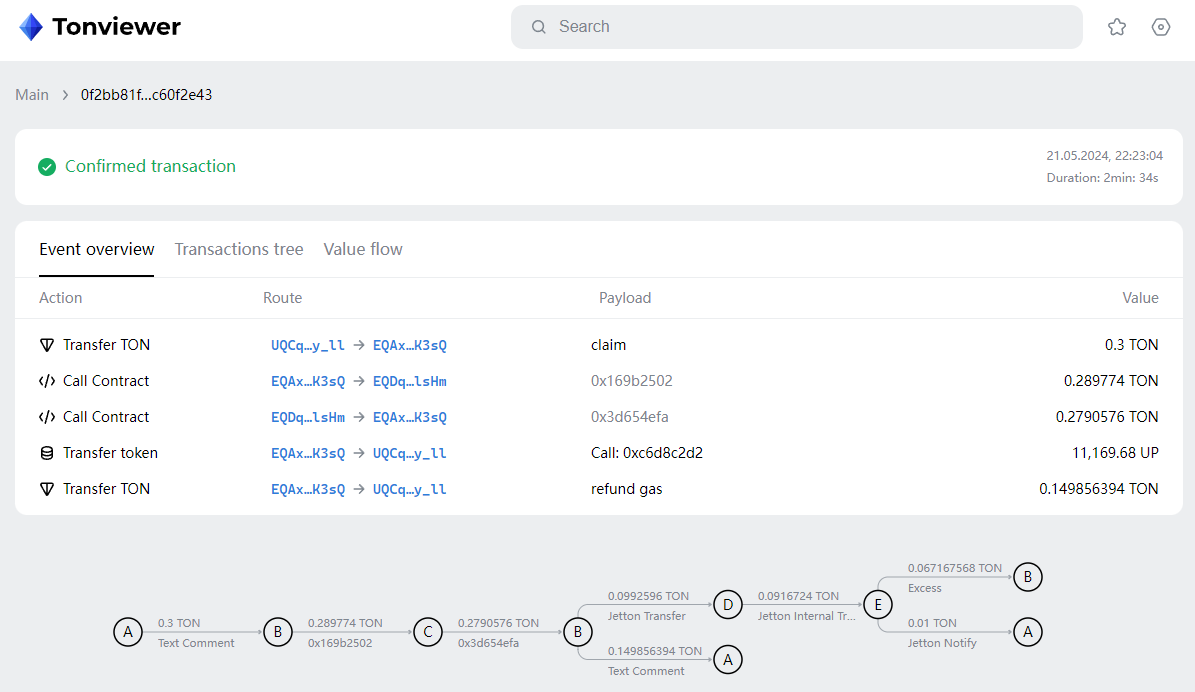
3.攻击者成功执行的claim交易整理如下:
窃取UP代币数量合计为:11169.68+20852.57+14677.88+25637.36+6311.49+50280.04+19720.52+50650.86+21700.89+8946.51=229947.8
4.后续白帽黑客notcoin-scam.ton发现了这一攻击行为并尝试救援出质押池合约中剩余的UP代币,并在约一天时间后向项目方tonup.ton发送链上消息进行汇报沟通。
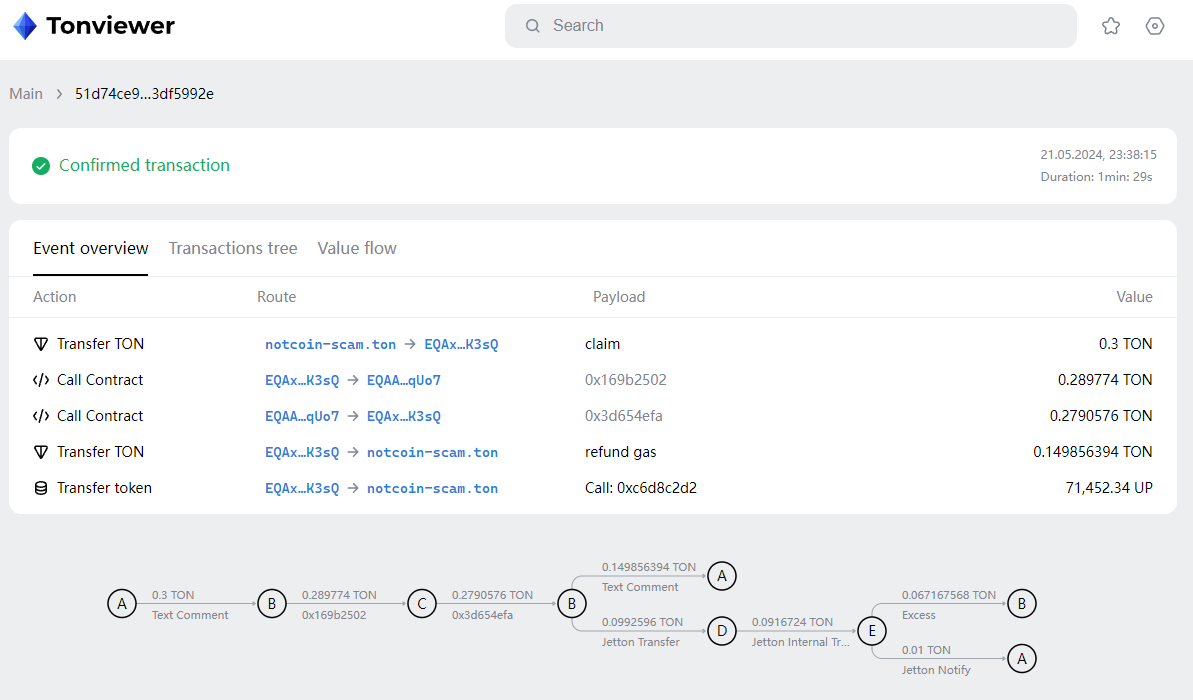
Transaction · 3618…d60e:"Hey, TonUp team, please DM me. I discovered a bug that was using by wallet UQCqfGGPYqDhFC2-6FcAldnWwkKHcs_Ez9RoXvJF_in3y_ll and tried to save at least some funds"
Transaction · a3be…1cff:"Hello, this is Leo from the TonUP team. Thank you for contacting us. Could you please guide us on how to proceed? We are pleased to offer rewards in appreciation of your support."
Transaction · 283a…2158:"Hello Leo! I apologize for the long response. Yes, I am ready to return the UP received, but there is one point. As soon as I saw that one of the wallets had found a vulnerability with the TONG pool, I had to act quickly and I withdrew some of my UP of their liquidity pool to STONfi. I then sent these UPs to the TONG pool and was able to collect some of the tokens. But then, in order not to lose tokens due to impermanent losses, I deposited UP back into the liquidity pool. You can look at my transaction history to see what I'm talking about. Now I am ready to return 35553.53 UP, and after completing the staking of UP (36610.13), which I contributed in order to save your funds, I will be able to return the missing part."
5.在此之前一段时间项目方向攻击者也尝试发送链上消息进行沟通,表示愿意提供 20%的金额作为赏金让其退还剩余的UP代币,但 48 小时的期限过后黑客似乎仍未退还被盗资产。
Transaction · 27d6…69cf:"Hello! You exploited a vulnerability in one of our smart contracts and unlawfully obtained a total of 229,947.8 UP in 10 transactions. Those funds belong to the users of the TonUP platform. You have 48 hours to return at least 183,958 UP to tonup.ton. If you act in good faith, we're willing to give you the remaining 20% UP as a bug bounty. Otherwise we will file a police report and try to recover the funds through legal actions."
6.值得注意的一点是,[黑客钱包-UQCqfGGPYqDhFC2-6FcAldnWwkKHcs_Ez9RoXvJF_in3y_ll]的初始资金来自于OKX 2,且窃取金额被全部转入Kucoin 1中,可以据此来查找到黑客的真实身份,以追回被盗资金。
此后项目方也是非常快速地关闭了质押池的claim功能并找到了一家审计公司TonBit来审计他们的Tact合约(合约仓库未开源),并且在两天时间内得出了一个审计报告,此事件告一段落。
我的推特@RealB1ue1nWh1te平时也会发一些安全相关的内容可以关注一波
- TITANX: The Tragedy of the Forced Investment Incident 523 浏览
- Penpie 被黑客攻击事件分析 655 浏览
- Dough Finance攻击事件---合约也有RCE 950 浏览
- SharkTeam:UwU Lend攻击事件分析 1081 浏览
- Euler Finance 攻击事件分析 1361 浏览
- 零时科技 || GPU攻击事件分析 1238 浏览
- 零时科技 || SATURN攻击事件分析 1257 浏览
- 【安全月报】| 4月区块链安全事件损失下降,因黑客攻击等造成损失金额达1.01亿美元 1106 浏览
- 零时科技 || SATX攻击事件分析 1105 浏览
- GFA 攻击事件 915 浏览
- 零时科技 || SumerMoney攻击事件分析 1053 浏览