如何解析uniswap v3下的muticall的data数据
- James
- 发布于 2022-04-20 00:18
- 阅读 9000
如何解析uniswap v3下的muticall的data数据
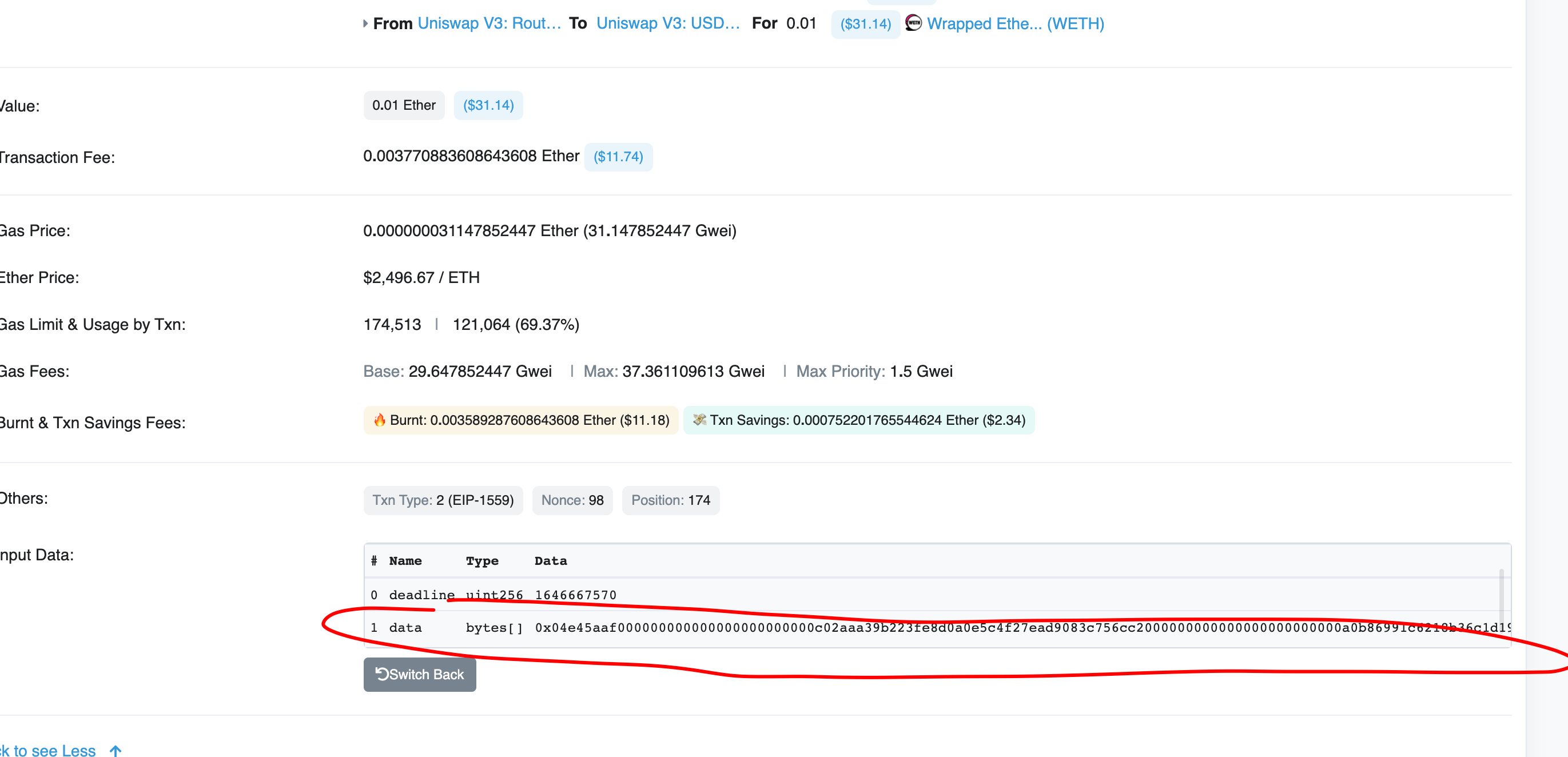 相信不少朋友在uniswap v3进行swap的时候,去etherscan上查看交易信息总会发现这个data是已传encode data, 如果你用utf-8去decode的时候,结果就如上图一样还是没有明文信息,今天就会交给大家使用web3.js的脚本去解析这个data字段,话不多说直接上教程:
1、我们先拿一笔交易来举例子:https://etherscan.io/tx/0x33104eedcad5fb2dbd2d8de49b8fee81c6e5b9d87cc43ba4d68fd2f55bcb1503
相信不少朋友在uniswap v3进行swap的时候,去etherscan上查看交易信息总会发现这个data是已传encode data, 如果你用utf-8去decode的时候,结果就如上图一样还是没有明文信息,今天就会交给大家使用web3.js的脚本去解析这个data字段,话不多说直接上教程:
1、我们先拿一笔交易来举例子:https://etherscan.io/tx/0x33104eedcad5fb2dbd2d8de49b8fee81c6e5b9d87cc43ba4d68fd2f55bcb1503
打开之后我们可以看到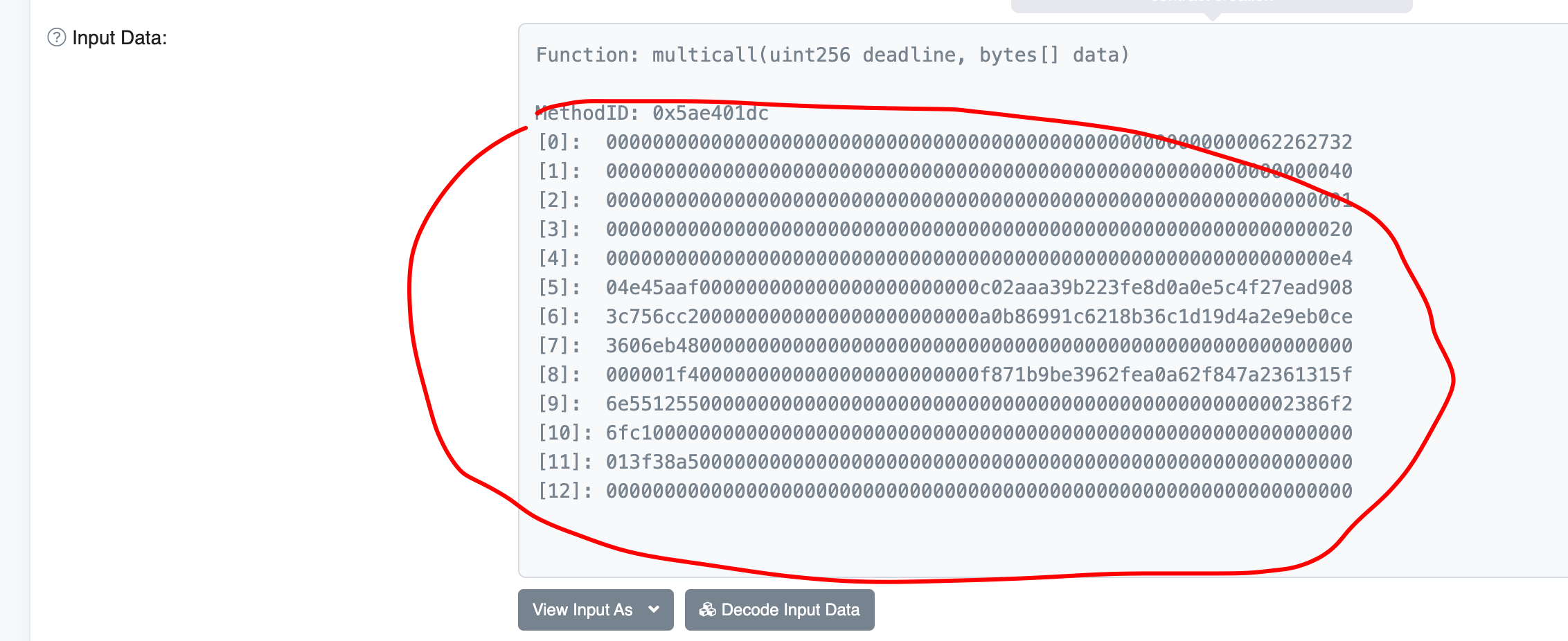 这里面有12 byte32的数据,接下来把这12行数据依次拼接出来组成如下的data数据:
这里面有12 byte32的数据,接下来把这12行数据依次拼接出来组成如下的data数据:
000000000000000000000000000000000000000000000000000000006226273200000000000000000000000000000000000000000000000000000000000000400000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000000000000000000000000000000000002000000000000000000000000000000000000000000000000000000000000000e404e45aaf000000000000000000000000c02aaa39b223fe8d0a0e5c4f27ead9083c756cc2000000000000000000000000a0b86991c6218b36c1d19d4a2e9eb0ce3606eb4800000000000000000000000000000000000000000000000000000000000001f4000000000000000000000000f871b9be3962fea0a62f847a2361315f6e551255000000000000000000000000000000000000000000000000002386f26fc1000000000000000000000000000000000000000000000000000000000000013f38a5000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000然后把这个数据放到我的这个脚本里:
const Web3 = require("web3");
const axios = require("axios");
const CALLDATA = "000000000000000000000000000000000000000000000000000000006226273200000000000000000000000000000000000000000000000000000000000000400000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000000000000000000000000000000000002000000000000000000000000000000000000000000000000000000000000000e404e45aaf000000000000000000000000c02aaa39b223fe8d0a0e5c4f27ead9083c756cc2000000000000000000000000a0b86991c6218b36c1d19d4a2e9eb0ce3606eb4800000000000000000000000000000000000000000000000000000000000001f4000000000000000000000000f871b9be3962fea0a62f847a2361315f6e551255000000000000000000000000000000000000000000000000002386f26fc1000000000000000000000000000000000000000000000000000000000000013f38a5000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000";
// const CALLDATA = "0000000000000000000000000000000000000000000000000000000000000020000000000000000000000000000000000000000000000000000000000000000200000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000000000000000000000000000000000000040000000000000000000000000000000000000000000000000000000000000008413ead5620000000000000000000000005c8cd1c2f2997f7a041026cc29de8177b4c6d8ec00000000000000000000000089e54f174ca5ff39cf53ab58004158e2ca012eac0000000000000000000000000000000000000000000000000000000000000bb8000000000000000000000000000000000035f2482336c0d4c2ba6e94faa1d66f000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000164883164560000000000000000000000005c8cd1c2f2997f7a041026cc29de8177b4c6d8ec00000000000000000000000089e54f174ca5ff39cf53ab58004158e2ca012eac0000000000000000000000000000000000000000000000000000000000000bb8fffffffffffffffffffffffffffffffffffffffffffffffffffffffffff2764c00000000000000000000000000000000000000000000000000000000000a11a8000000000000000000000000000000000000000000000000000000e8d4a510000000000000000000000000000000000000000000000a56d35c029fd16645e079000000000000000000000000000000000000000000000000000000e840308c030000000000000000000000000000000000000000000a503344abc0fbe23670910000000000000000000000005a2b5cb4ce921abd65f0c66c2c839894bfc2076c000000000000000000000000000000000000000000000000000000006244356a00000000000000000000000000000000000000000000000000000000"
const web3 = new Web3();
function extractParameters(signature) {
let params = [];
const allParameters = /\b[^()]+\((.*)\)$/gm;
const splitParameters = /((\(.+?\))|([^,() ]+)){1}/gm;
let _allParameters = allParameters.exec(signature)[1];
while ((match = splitParameters.exec(_allParameters))) {
params.push(match[0]);
}
return params;
}
async function decode(calldata) {
let calls = web3.eth.abi.decodeParameters(['uint256', 'bytes[]'], calldata)[1];
for (let index = 0; index < calls.length; index++) {
let call = calls[index].replace("0x", "");
let selector = call.slice(0, 8);
let data = call.slice(8);
let request = await axios.get(
`https://www.4byte.directory/api/v1/signatures/?hex_signature=${selector}`
);
let signature = request.data.results[0].text_signature;
console.log()
console.log(`步骤 ${index}, 方法: ${signature}`);
let parameters = extractParameters(signature);
let decoded = web3.eth.abi.decodeParameters(parameters, data);
for (let i = 0; i < parameters.length; i++) {
console.log(` 参数 ${i} - 类型: ${parameters[i]} - 值: ${decoded[i]}`);
}
}
}
decode(CALLDATA);这个脚本的原理就是使用
https://www.4byte.directory/api/v1/signatures的api来对function的前4个字节去数据库里查找对应的明文信息,然后解析出来打印在控制台里,可以看我下面的执行结果:
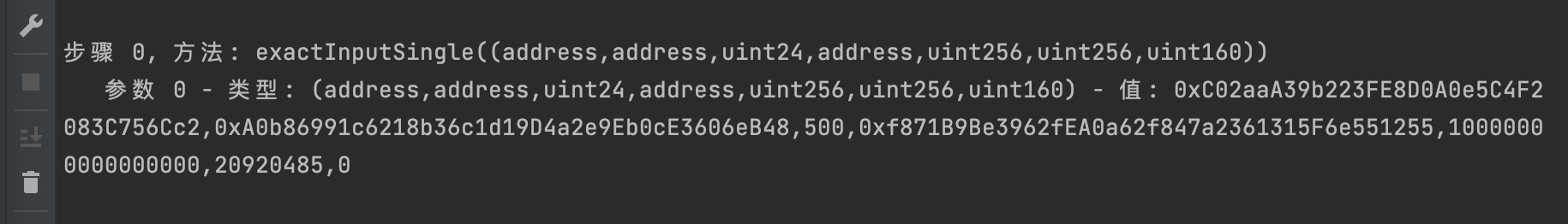
- 学分: 114
- 分类: Uniswap
- 标签: multicall Uniswap V3
点赞 8
收藏 11
分享
本文参与登链社区写作激励计划 ,好文好收益,欢迎正在阅读的你也加入。
- 《Uniswap V3 开发指南》上线,一本把 Uniswap V3 讲“透”的电子书 407 浏览
- 跨合约调用 1661 浏览
- Multicall:批量调用合约 1398 浏览
- Uniswap v3:集中流动性、JIT攻击与集成指南 1465 浏览
- Uniswap v3 中的 Position 3410 浏览
- Panoptic 的演变:从 V1 到 V2 546 浏览
- NFT 仓位 312 浏览
- 在Uniswap V3代码库中计算两个价格之间的真实储备量 1090 浏览
- NFT ManagerContract 227 浏览
- 兑换费用 279 浏览
- 价格预言机 295 浏览
- 不同的价格范围 278 浏览
4 条评论
请先 登录 后评论

