Security Incidents Analysis
2024年11月26日更新
13 人订阅
DCF&DCT tokens: The Tragedy of the Forced Investment Incident(2)
- Lorrie
- 发布于 2024-11-26 17:35
- 阅读 2284
On November 24, 2024, the protocol associated with DCF and DCT tokens was attacked, resulting in a total loss of $440K on the BSC.
Root Cause
- The DCF token’s transfer mechanism enforces a forced investment. When the DCF token is sent to the the USDT-DCF liquidity pool, 5% of tokens are automatically swapped for USDT within the same pool and then added as liquidity to the USDT-DCT pool. This action triggers a swap in the USDT-DCT pool, which can be manipulated, enabling attackers to execute sandwich attacks for profit.
- Note that in this attack, "forced investment" means forcing the protocol to execute swaps at outrageous prices.
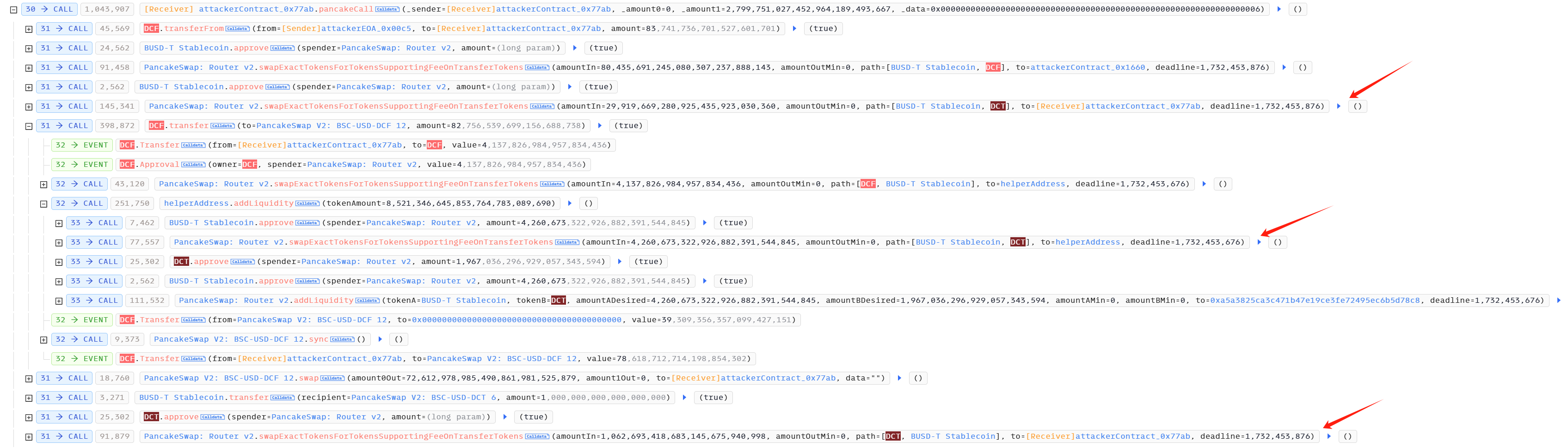
Attack Steps (based on the tx )
- The attacker borrowed approximately 110,355,370 USDT tokens through a flash loan. Using these funds, the attacker executed two swap transactions to manipulate the
PancakeSwap V2: BSC-USD-DCF 12andPancakeSwap V2: BSC-USD-DCT 6pools. The first transaction allowed the DCT liquidity helper to receive a significant amount of USDT during subsequent DCF token transfer processes. The second transaction was executed as a front-run attack. The price difference between the swaps is shown below: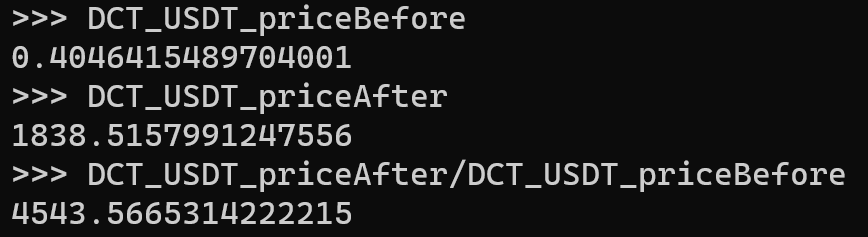
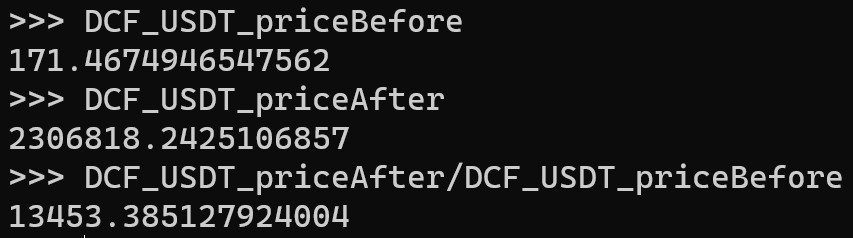
- The attacker transfers DCF tokens to the USDT-DCF pool, triggering a swap that converts 5% of the tokens into USDT. Due to the manipulation, a large amount of USDT is received by the DCT liquidity helper, which it subsequently used to execute a swap on the USDT-DCT pool.
- The attacker swapped DCT to USDT on the USDT-DCT pools as a back-run attack and made a profit.
Ref
点赞 0
收藏 0
分享
本文参与登链社区写作激励计划 ,好文好收益,欢迎正在阅读的你也加入。
0 条评论
请先 登录 后评论
